[PWN] NullConCTF 2025 - hateful2-challenge
( بِسْمِ اللَّـهِ الرَّحْمَـٰنِ الرَّحِيمِ )
Hoy, it's a heap challenge from Nullcon CTF 2025 ;-), Thanks to Saif (@wr3nchsr).
What will we try to do?
- Reversing the Binery
- List what we found.
- Exploit
- Leak the libc address using unsortedbin
- Leak heap address and do (mangling/demangling)
- Overwrite the next pointer of the free list
- Control the RIP with ROP-Chain
Let's start ;-).
Reverse the Binary
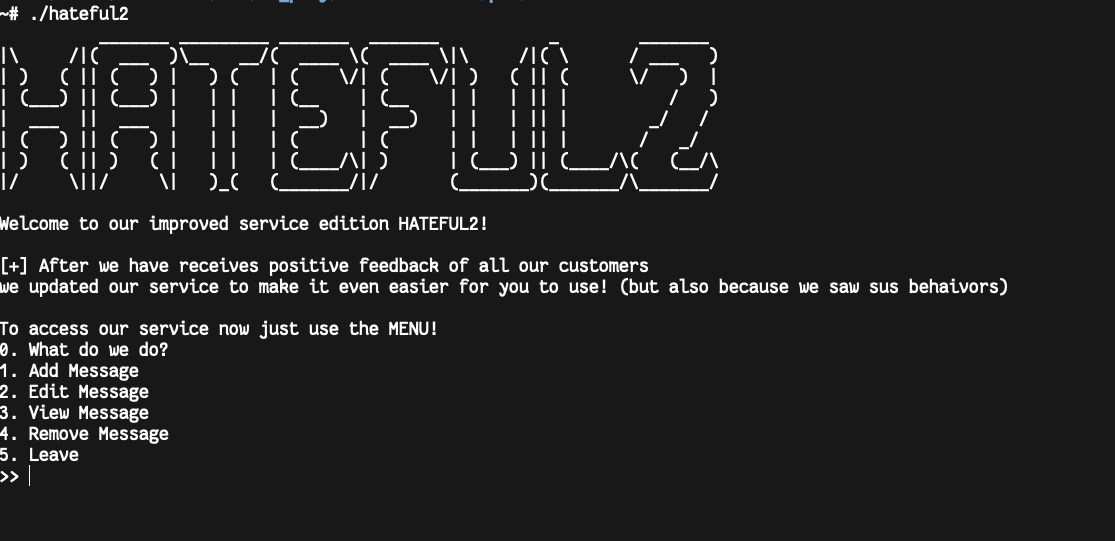
after reversing the binary and the following screenshots are samples,
we have 5 options to interact with the binary:
- what do we do? (about_us)
- add message (malloc)
- edit message
- View message
- remove message (free)
- leave (exit)
- we can control the allocation size without limit
- we have a leak in (about_us) function to a variable on the stack (stack-address).
- there is Use-After-Free (read & edit) after free()ing the chunk.
- the libc version is 2.36 (there is a protection on the free list addresses).
Exploit
first will set the script to interact with the binary easily (for us)
First, we will call (about us) function and take the stack address as the first leak.
We can control the size of the allocation so we can add a chunk to any bin, so to do a leak we will use the unsorted bin because when we free it the free list is stored in something called (main arena) and this is on the libc so we will get a leak from it.
Easily we will create a large allocation (0x1000) and after it we will create a small one (0x10) this small chunk is a guard and it used to protect our chunk from being consolidated with the wildness of the heap (if this is hard xD you can leak all of that from pwn.college), so we will free the large chunk and the main arena address will be stored in the chunk so using the UAF we will read from the free()ed chunk which contains the libc address and with we have our second leak
Now we will leak a heap address because it will be used to mangle and demangle the addresses before putting it into the free list to overwrite the next chunk address (got these functions from pwn.college modules too - you can check the libc source code to understand the logic)
after leaking the heap address and controlling the list we will try to:
- allocate a chunk on RIP
- modify the chunk to overwrite the address that we will jump to















Comments
Post a Comment