[PWN] LA CTF 2025 - gamedev heap challenge
( بِسْمِ اللَّـهِ الرَّحْمَـٰنِ الرَّحِيمِ )
Hey guys,
now we have a challenge from LA CTF 2025 it was an easy but hard -I made a mistake :(-, let's start.
Reverse (code review)
in the reverse process, we can notice the following
- the binary uses a struct called "Level"
- there is a heap overflow.
- no free in the challenge
- custom list (next-ptr) is used
functions in the binary
- "init" creates a chunk to store the next addresses and this is the "start" variable
- "explore" function is used to move from level to level.
- "create" creates a new chunk with size "0x60"
- "test" to read from the chunk
- "edit" modify the chunk "vulnerable to overflow"
- "reset" is used to reset the "curr" pointer which points to the currently used level. "remember this"
what I got from using the binary
- to point to a level you have to create a level after it
- the "create" function adds the pointer of new levels "curr->next[idx] = level;" in the current level's next
- we have to
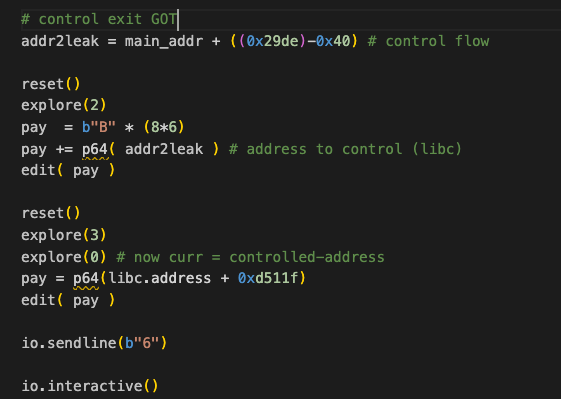
- leak the libc
- control the RIP (with one gadget)
Exploit
my mistake was that I used the "reset" function each time I created or used any function and this was wrong because the function set "curr = start" and the start chunk we can not control.
the idea is:
- create some levels 3 levels [2,3,4]
- use "explore(3)" to point to level "3" chunk
- create level [0] and the address of it will stored in level 3's next
- point to level 2 using "explore(2)"
- use "edit" to write into the current level which is 2
- with overflow in the edit function, we can modify the next pointer which is stored in level 3
now with these steps, we can control the next pointer so we can have arbitrary read & write when we add an address to the next variable it is considered as a level so we can read(leak libc) or write(on address) on it.
let's take a look at the memory, the red chunk is "start" and we can not control it, the blue chunk is the level with index "2", and the green chunk is the level "3" which is corrupted from us.
something to add the index is pointing to the place in the space of "next" from 0 to 7.
when we point to the corrupted level with our address it will be stored in the first place of the next list of level 3 so the index will be "0".
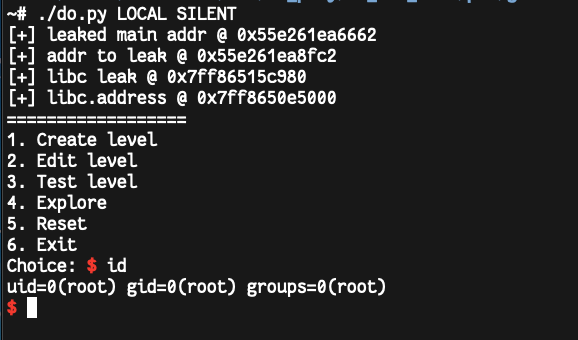
and if we contain all of these parts together we will get the shell ;-).
the output of one gadget
Thank you for reading, the challenge and solver in my GitHub (will be isA).
Update: all challenges are here.
عن أبي هريرة رضي الله عنه أن رسول الله صلى الله عليه وسلم قال: (قال الله عزوجل: كل عمل بن آدم له إلا الصيام؛ فإنه لي وأنا أجزي به، والصيام جنّة، وإذا كان يوم صوم أحدكم فلا يرفث، ولا يصخب، فإن سابّه أحد أو قاتله فليقل: إني امرؤ صائم، والذي نفس محمد بيده لخلوف فم الصائم أطيب عند الله من ريح المسك، للصائم فرحتان يفرحهما: إذا أفطر فرح، وإذا لقي ربه فرح بصومه) رواه البخاري ومسلم.
.














Comments
Post a Comment