Lets Analysis STM32F103 Chip Firmware from Attify
Let's start our blog.
As we know any IoT device should have a firmware to run it and there is a thought that it is secure by default because it is in a board, but we know that we can dump this firmware, our firmware know is already shared with us something like training to learn basics of reversing firmware.
you can download the firmware from here.
if we run the file command on the firmware we will find this "STM32F103C-firmware.bin: data" and if we try to get the architecture using binwalk it will return empty result "binwalk -A STM32F103C-firmware.bin" but we don't need this because it is a famous chip and we can know what we want from google.
After searching for the chip name STM32F103C we will open its default page you will know that it run using "ARM Cortex M3" we will need that later, it is time to analysis using Ghidra.
Analysis
Dropping the firmware file to Ghidra but it will not detect anything about the binary
take a careful look in the following screenshot you will see that the pointer is in red this means this is an invalid pointer and if you search more you will not get any useful thing from this analysis.
so we have to write the memory map by our selves we will search for the datasheet of this Chip and check the memory map from it.
from this map we can know that flash start at "0x08000000", SRAM start at "0x20000000" and its size is 20Kbytes = 0x5000, and Cortex-M3 internal peripherals "0xE0000000 -> 0xE0100000".
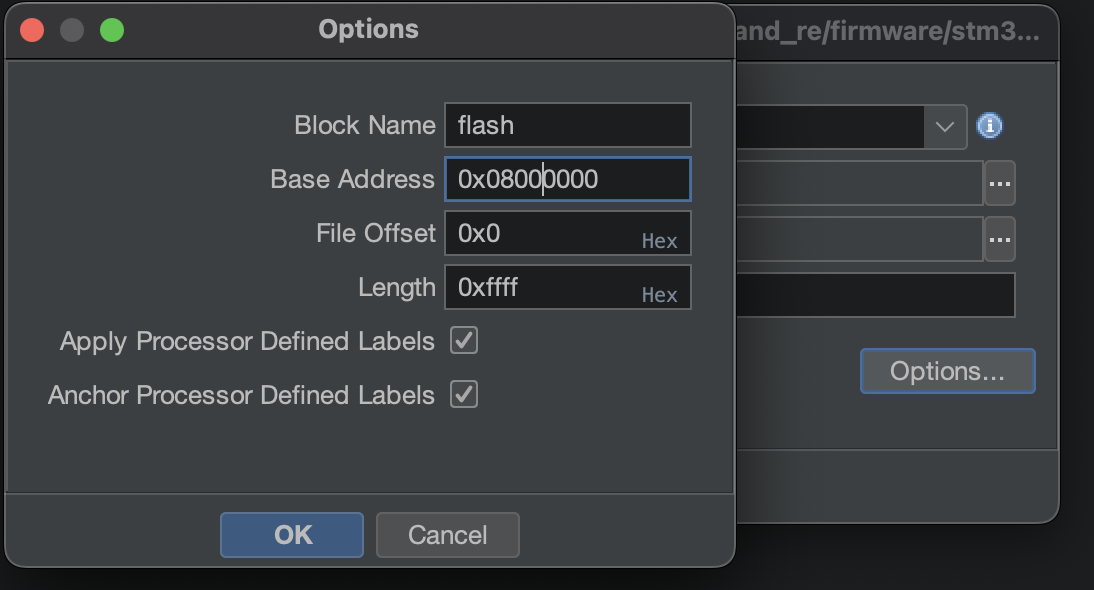
Let's start analysis again by dropping the firmware to Ghidra but now we will add the start of flash before opening the firmware
now we can open firmware again but without auto analysis this time we have to do something first which is building the memory map from Ghidra we can open the "Memory Map" tab and add SRAM and peripherals that we mentioned before.
Note that we can use the SVD-Loader Ghidra Plugin with these Chips but in this example, we will ignore it in some cases, it is very useful and helps with analysis.
Searching in binary strings we can find a key to start with
following this i got two functions "auth_success()" and "auth_fail()"
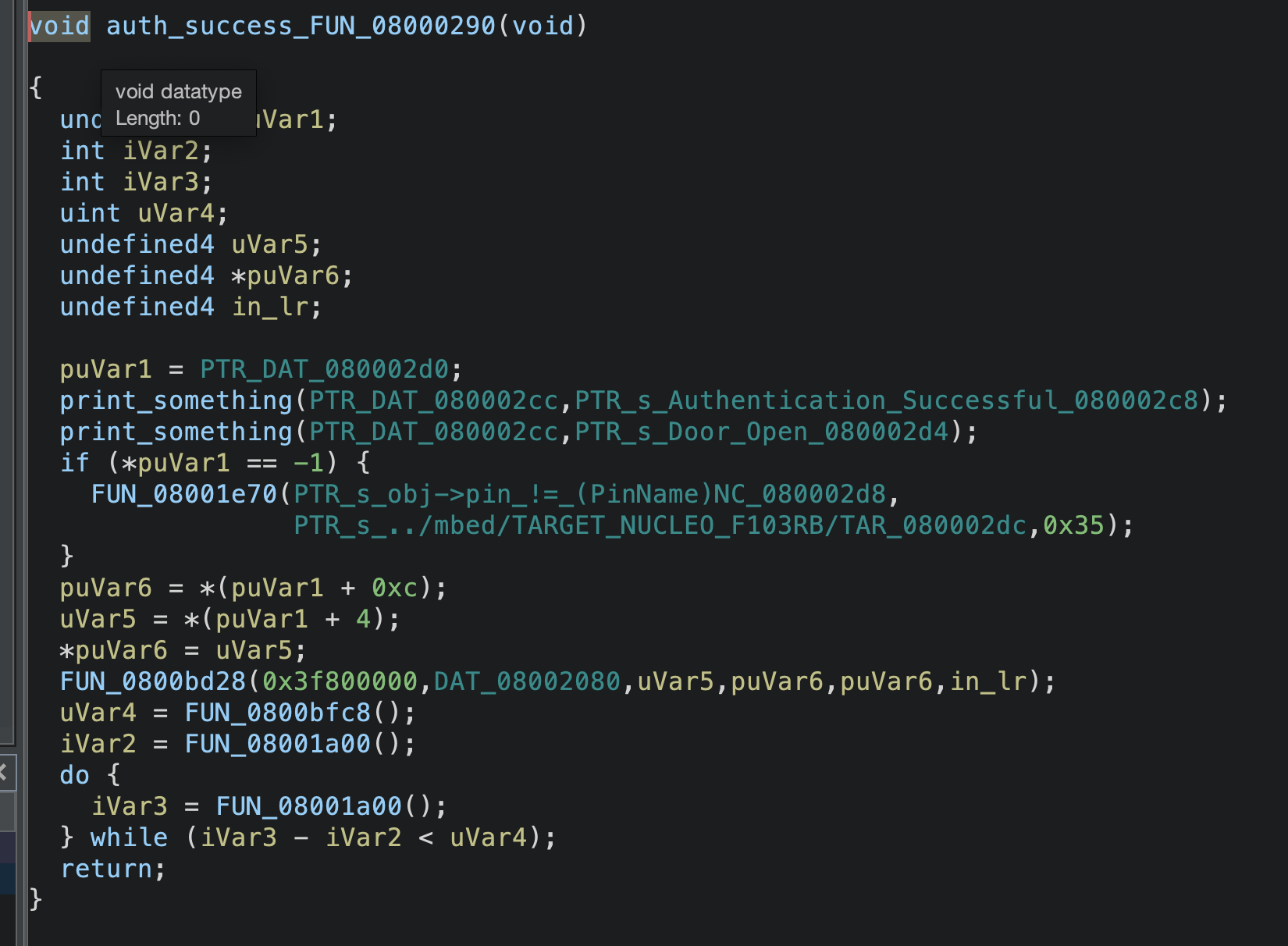
but we can not find where these functions are called? so you have to know now Ghidra sometimes can not find all functions so we have to do some manual things by searching around the functions and i found this part which gives me two important functions, stop on it and click (d) in Ghidra to decompile this part if possible
and i got these functions
after clearing it we can find this
we can ignore any function that will not lead to our end goal, For the Authentication message we can find the function using strings too
let's analysis function "FUN_08000300" or "FUN_080007ee" it prints the string message about entering a password so this is the interesting part and the call of function "FUN_080002e0" which have the authentication check that we are targeting.
the "iVar1" contains the output of the function "FUN_08003910" which have our input(maybe) and some pointer to a string, trying to analyze the function but it was a mess
so what I think is this is a function that looks like "srcmp" to compare the password with my input so that we can know where that the string that this pointer points to is the password that we need (maybe).
This is not the end you can try your way, you can do it better than me and I'm not sure that this is the password yet i don't have the board with me to be sure but this is what i ended with.
if you wanna try the same technique in different firmware you can check this arm-bare-metal-1 it is like a CTF challenge.
Thank you.
عن أنس بن مالك رضي الله عنه عن النبي صلى الله عليه وسلم قال: (لا يؤمن أحدكم حتى يحب لأخيه ما يحب لنفسه) رواه البخاري ومسلم





















Comments
Post a Comment